If you’re wondering, “What is a Proxy Server? How does it work?” this article will help you understand it. Learn about its types, functions, and Authentication, and how you can use a proxy server to mask your online identity. We use internet a lot these days, whether it’s on a PC, a laptop, or on your smartphone. So, protecting your privacy is very important, especially when you use smartphones for all your work and transactions. Authentication is a significant part of online privacy, so making sure you have the right type of proxy server can protect your online activity. You can use a reliable VPN service like Surfshark.com on your phone too for maintaining your online privacy.
Functions
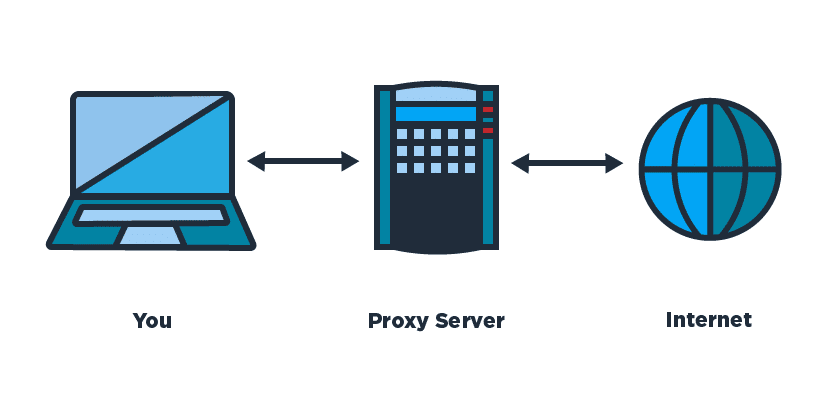
A proxy server acts as an intermediary agent between the requester and the destination host. The client does not directly send the request to the host; instead, it sends it to the proxy server. The proxy then sends the request to the destination and returns the data to the client.
A proxy server is responsible for blocking identity theft, which is a major problem in today’s Internet usage. The proxy server reads network users’ location information and generates a dummy identity, which is associated with the user’s identity. The server then stores this relationship in its memory storage and forwards the content to the appropriate network user. However, there is one significant disadvantage to this type of service. As a result, it can only block certain websites.
Types
There are several types of proxy servers, and knowing which one to use can help you ensure a fast, reliable connection. There are two basic types: shared and dedicated. Shared proxies share server resources with other users and are therefore prone to blacklisting. Dedicated proxies are usually used for sensitive websites, such as government or educational institutions. However, they can be dangerous if they’re blacklisted, among other internet dangers. This article will discuss both types.
Public and data center proxies are two types of proxy servers. Public proxies are freely accessible over the internet, allowing everyone to browse anonymously. However, public proxy security is not up to the mark, and the main disadvantage of these servers is that they’re often unsafe and don’t protect user data. Datacenter proxies are located in a data center and are more secure. They’re designed to route designated traffic through one server.

Authentication
You must use a primary authentication mechanism when configuring authentication on a proxy server. This should correspond to a section in the config file titled “client”. If there is only one “client” section, you should specify only one primary authentication mechanism. For multiple “client” sections, specify the primary authentication mechanism for each. This will ensure that only authenticated users can connect to the proxy server. You can add additional domain controllers as “host_3”, “host_4”, etc.
IP authentication is another type of authentication. It grants or denies access to a proxy server based on IP address. The proxy server has a configuration file that lists the accepted IPs. If your IP matches one of those listed in the configuration file, you’ll be able to connect. If you don’t see the “proxy” sign, you’ve already passed authentication. Then, you’re ready to browse the web.
Using a proxy server to mask your online identity
Using a proxy server to mask your internet identity is an excellent way to keep your identity and online behavior private. This is because it can allow you to appear on a different computer. You can also use a proxy to access content that is restricted to certain locations. If you are worried that your internet activity will be tracked by a company, a proxy can protect you against such an attack. These services are free, but you have to be careful when using them.
A proxy serves two purposes: to hide your online identity and to improve internet speed. It can also be used for privacy, as some proxies can block access to certain websites. Another function of a proxy is to protect your privacy online by masking your IP address. By using a proxy, you will be able to access websites that are blocked for people with certain IP addresses. You can also protect your online identity by using a proxy to browse blocked websites and keep your Internet traffic safe.